WordPress creates nearly 50% of the websites you visit on the Internet. It is the go-to website software for Intrada. It is used by businesses and governments around the world. Almost every website we create from scratch is a WordPress-made website. So, let’s review what WordPress is and how it can ...
Strong, Safe Passwords – Your First Line of Cyber Defense
Information Technologies | David Steele | Tuesday, May 31, 2022
Technology is now part of everyday life for the majority of people around the world.
Passwords protect sensitive parts of technology. From user accounts to bank accounts, pin numbers to garage door keypads, cell phones to store cards—all of the data is protected by passwords.
Remembering all those passwords can be quite a task. When the plethora of passwords you must remember are coupled with requirements to change passwords every 30 days, specifications that require a crazy combination of characters, requirements that you can’t use old passwords, or limitations that you can’t use words or phrases—what a headache!
Password Fatigue is Real and Justifiable

A study by LastPass found that 80 percent of respondents were concerned about passwords being compromised, but 50 percent of that same group had not changed their passwords. LastPass accredits this paralysis to password anxiety and fatigue.
Password fatigue is defined as a feeling of exhaustion or resistance to creating and using complex passwords. It is real and understandable!
With regular news of data breaches, phishing scams and increased cyberattacks from around the world, it can be exhausting to remain vigilant. Maintaining strong passwords is critically important to your cybersecurity though.
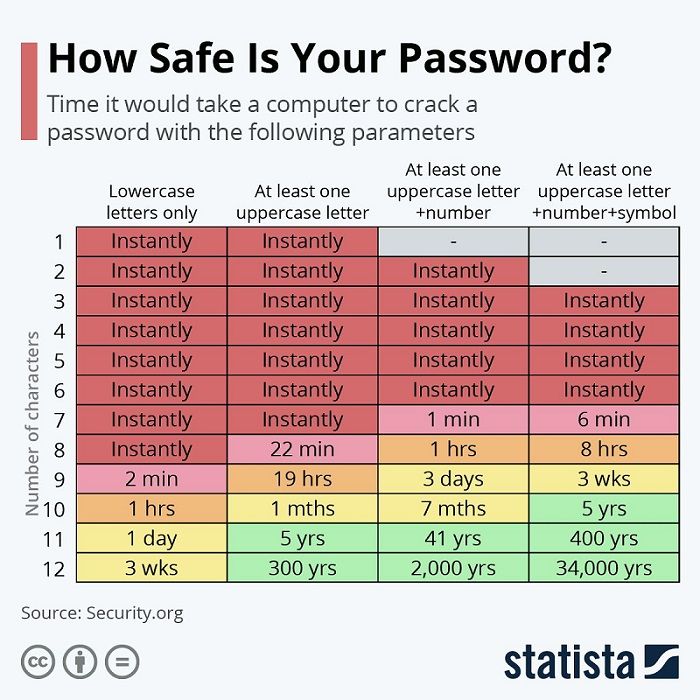
Statistics about the quality of password selection and usage are not great. In 2021, the top 200 passwords identified by NordPass in their yearly report were, well, kind of dumb. All 200 passwords identified took under 10 seconds to crack. Yikes!
Coming up with a memorable password is difficult. Just when users think they have a password system, often their tech department adds on
Passwords Provide Protection
If you knew there were roving bands of international criminals attacking homes and businesses in your neighborhood, would you leave your key under the front mat? Or in the mailbox? Or leave your backdoor unlocked? Of course not. We all want to protect ourselves and the people and things we care about.
This is why passwords are so important. The bottom line is passwords are the keys and hackers want yours.
According to IBM's 2021 Cost of a Data Breach Report, 85 percent of phishing attacks went after user credentials—user names and passwords—and 20 percent of data breaches were started because of compromised credentials. Powerful passwords provide protection.
There are Just so Many Passwords…
How do you create powerful passwords, store them securely and actually remember them—without having them posted on a bulletin board or sticky note next to your computer?
Microsoft recommends that passwords have 12-14 characters and a combination of upper and lowercase letters, numbers and symbols. It could be a combination of words, names, numbers, but should not just be one name or word.
We have a guy in the office that can remember passwords. We aren’t sure if that is a gift or curse, but it is impressive! Most people need help remembering their passwords. Others use password generators to create passwords. We recommend password generators when using a password manager.
Some people have a little black book with regular passwords. Intrada staff also use a password manager—actually multiple password managers containing passwords to manage clients’ password managers. It can be complicated.
So, what is the best way to manage passwords? Intrada recommends a password manager. In the corporate environment, it’s a no brainer. Pay the money to get a business subscription and each user will have an account to manage their passwords and share passwords. Do not share password manager accounts.
In the personal world, get a family subscription so your spouse, kids and parents can access information in an emergency. Finally, have a hard copy export in a safe that is updated several times a year.
Password Manager Safety
The big question Intrada often hears is this: Is it safe to have all my passwords in a password manager? What if the password manager gets hacked and they get all my passwords?
Intrada looks at passwords managers the same as other security items in life. Nothing is foolproof, but password managers are designed specifically to protect your passwords. Password managers have the best protection and systems in place to monitor activity on your account. They are much safer than a little black book that could be lost, a notepad file on a phone that could be copied, or a file stored on a computer or in the cloud.
Don’t Forget to Protect the Computer in Your Pocket
Another item that should be protected is your cell phone. Many systems and accounts can be accessed with information or notifications from cell phones. You need to password protect your phone and guard it like your car keys or credit cards.
Caring is Not Sharing
Sharing passwords is a bad idea. It is also important to use different passwords in case one password gets compromised. This way the damage is limited to that one account.
Recommended Password Managers
LastPass has an easy-to-use password generator: www.lastpass.com/features/password-generator
Protect Those Passwords
Passwords are very important and the first line of defense against unauthorized access to accounts and systems. Whenever possible, add on
Intrada Technologies offers security audits for organizations. Intrada security audits are comprised of two key areas—a security assessment and personalized, physical inspection. Following the audit, you will receive the assessment results and review them with a dedicated project manager or network engineer. Problem areas will be shared and potential solutions offered.
Or, if you need assistance implementing a corporate password manager, Intrada can help.
Contact Intrada for your IT and cybersecurity needs by calling 800-858-5745 or by filling out the contact form below.

Cybersecurity Awareness Poster
What is an MSP, and how can it help your busi...
There are so many acronyms in the information technology industry – AP, API, FTP, IP, and the list goes on and on. If you do not want to remember any of these acronyms anymore, look to this, hopefully, last acronym: MSP.An MSP is short for managed service provider. It is a third-party company that r...
Contact Us
- 800-858-5745
31 Ashler Manor Drive
Muncy, PA 17756
Office Hours
Monday - Friday
8 AM - 5 PM EST
Intrada Technologies


Copyright © 2025 - Intrada Technologies - Privacy Policy and Disclaimer
Our website uses cookies and analytics to enhance our clients browsing experience. Learn More /
