The
Cybersecurity Maturity Model Certification
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
(
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
) program enhances cyber protection standards for the Defense Industrial Base companies. It is designed to protect sensitive unclassified information shared by the Department of Defense (DoD) with its contractors and subcontractors. Additionally, the program incorporates cybersecurity requirements into acquisition programs and provides the DoD. Increased assurance that contractors and subcontractors are meeting these requirements.
What is
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
?
Source: https://dodcio.defense.gov/Portals/0/Documents/
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
/ModelOverview_V2.0_FINAL2_20211202_508.pdf
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
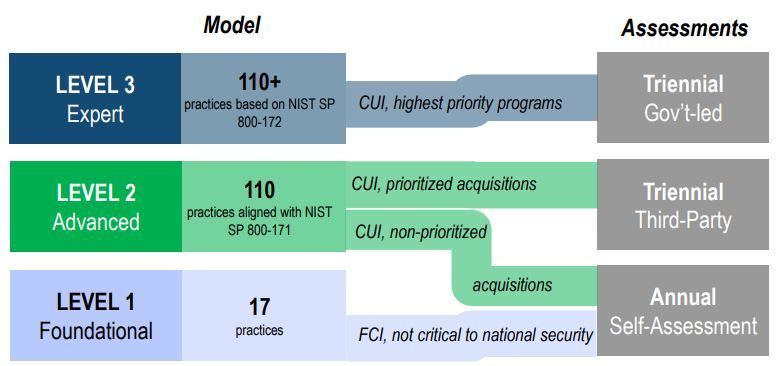
is a tiered model for companies entrusted with national security information to implement a cybersecurity standard at progressively advanced levels depending on the type of sensitive information required to complete the government or vendor contract.
In September of 2020, the DoD published an interim rule to the Defense Federal Acquisition Regulation Supplement (DFARS) in the Federal Register, which implemented the DoD’s initial vision for the
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
program (
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
1.0). The interim rule became effective on November 30, 2020, establishing a five-year phase-in period.
In March 2021, the DoD initiated an internal review of
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
’s implementation, informed by more than 850 public comments in response to the interim DFARS rule to refine policy and program implementation.
In November 2021, the DoD announced
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
2.0, an updated program structure and requirements designed to achieve the primary goals of the initial review.
How does
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
affect my company?
Companies will be required to comply with the new rulemaking once the forthcoming rules go into effect.
As of January 2021, the DoD is still pursuing rulemaking and has suspended the current
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
Piloting efforts and will not approve the inclusion of a
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
requirement in any DoD solicitation.
The DoD encourages contractors to continue to enhance their cybersecurity posture during the interim period while the rulemaking is underway.
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
bases the control and protection of Controlled Unclassified Information (CUI). CUI is information that requires safeguarding or dissemination controls consistent with applicable laws, regulations, and Government-wide policies but is not classified.
Intrada moves all network security standards to a
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
2.0 on a LEVEL 1 (Foundational) and partial LEVEL 2 (Advanced) based on the clients’ business focus and requirements.
How can Intrada Help?
Intrada also considers Protected Health Information (PHI) under The
Health Insurance Portability and Accountability Act
The Health Insurance Portability and Accountability Act (HIPAA) is a critical piece of legislation in the United States aimed at protecting sensitive patient health information. Enacted in 1996, HIPAA established comprehensive standards for the privacy and security of medical data, ensuring that healthcare providers, insurers, and other related entities handle patient information responsibly. The Act sets national standards for electronic health care transactions and addresses the security and privacy of health data. It is essential for organizations handling health information to comply with HIPAA regulations to safeguard patient privacy and ensure the integrity and confidentiality of the data. https://www.hhs.gov/hipaa/index.html
(
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) is a critical piece of legislation in the United States aimed at protecting sensitive patient health information. Enacted in 1996, HIPAA established comprehensive standards for the privacy and security of medical data, ensuring that healthcare providers, insurers, and other related entities handle patient information responsibly. The Act sets national standards for electronic health care transactions and addresses the security and privacy of health data. It is essential for organizations handling health information to comply with HIPAA regulations to safeguard patient privacy and ensure the integrity and confidentiality of the data. https://www.hhs.gov/hipaa/index.html
) Privacy Rule to follow the exact safeguarding requirements. PHI is health information in any form, including physical, electronic, or spoken information. Essentially, all health information is considered PHI when it includes individual identifiers.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) is a critical piece of legislation in the United States aimed at protecting sensitive patient health information. Enacted in 1996, HIPAA established comprehensive standards for the privacy and security of medical data, ensuring that healthcare providers, insurers, and other related entities handle patient information responsibly. The Act sets national standards for electronic health care transactions and addresses the security and privacy of health data. It is essential for organizations handling health information to comply with HIPAA regulations to safeguard patient privacy and ensure the integrity and confidentiality of the data. https://www.hhs.gov/hipaa/index.html
is a federal law that requires the creation of national standards to protect sensitive patient health information from being disclosed without the patient's consent or knowledge.
Following the
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
standard as a benchmark for policy and procedures has allowed Intrada to create cyber security plans for our clients that handle compliance requirements for Cyber Insurance Policies,
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) is a critical piece of legislation in the United States aimed at protecting sensitive patient health information. Enacted in 1996, HIPAA established comprehensive standards for the privacy and security of medical data, ensuring that healthcare providers, insurers, and other related entities handle patient information responsibly. The Act sets national standards for electronic health care transactions and addresses the security and privacy of health data. It is essential for organizations handling health information to comply with HIPAA regulations to safeguard patient privacy and ensure the integrity and confidentiality of the data. https://www.hhs.gov/hipaa/index.html
Enforcement, future
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
assessments, Criminal Justice Information Services (CJIS), and good corporate cyber hygiene.
Starting with a standard and removing items that do not apply has allowed a more complete policy, procedure, and management process.
Intrada continues to work for clients through
CMMC
The Cybersecurity Maturity Model Certification (CMMC) is a standardized framework developed by the United States Department of Defense (DoD) to enhance and ensure the cybersecurity posture of its supply chain. The CMMC specifies a set of cybersecurity practices and processes that defense contractors must implement to protect controlled unclassified information (CUI) and federal contract information (FCI) within their systems.
The CMMC framework is detailed and tiered into five maturity levels, each with increasing demands for cybersecurity hygiene:
Level 1 (Basic Cyber Hygiene): Requires basic cybersecurity practices to safeguard FCI.
Level 2 (Intermediate Cyber Hygiene): Introduces additional practices to protect CUI and begins the transition to more advanced controls.
Level 3 (Good Cyber Hygiene): Focuses on a comprehensive set of cybersecurity practices to implement and maintain good security posture for CUI.
Level 4 (Proactive): Adds more sophisticated and proactive measures to detect and respond to emerging threats.
Level 5 (Advanced/Progressive): Emphasizes highly advanced and optimized practices to protect CUI from advanced persistent threats (APTs).
The primary goal of the CMMC is to reduce the risk of cyber threats and ensure that defense contractors adhere to robust security standards. Companies seeking to participate in DoD contracts must undergo assessment by an accredited third-party organization to achieve the necessary CMMC level for their specific projects.
Adopting the CMMC framework not only fulfills compliance requirements but also reinforces overall security practices, helping organizations safeguard sensitive information and maintain the integrity of their operations.
Self-Assessments and create policies and procedures to enhance cyber security practices and network security practices and implement employee awareness and training programs.
If you are interested in learning more about Intrada’s approach to Network Management and how we handle Cyber Security and Compliancy, contact our Client Services Team today.
Intrada Technologies client services team: David Steele, Rachel Edwards, Nicole Keiner, and James Haywood
Sources



